utwritelookup
With utwritelookup a Splunk user is able to write the results of a Splunk search to a lookup in Cribl Stream. Both .csv and .gz lookups are supported. Please note that the command takes all fields given in the results sent to the command and does not provide any multivalue handling. As the command has to run on the search head with the full resultset, the command is of type Eventing. As Cribl Stream does not provide any functionality to edit a lookup, the whole file is sent to Cribl Stream even if only a single value changes. If the lookup already exists in Cribl Stream the file is overwritten.
For utwritelookup to push an updated lookup to the worker nodes following conditions have to be met:
- There was already a configuration deployed to the worker group
- There are no committed but not deployed changes
If there are commited but not yet deployed changes, utwritelookup creates a n ew commit. If there are files edited but not committed, utwritelookup only commits the changes done by itself.
Arguments
| Name | Description | Example | Default |
|---|---|---|---|
| instance | Instance into which the created lookup should be written, supports multiple instances in a comma seperated list | dev | - |
| lookup_name | Name of the lookup that should be created or updated in Cribl Stream. The lookup name has to end in .csv or .gz | ip_ranges.csv | - |
| append | If the events piped into utwritelookup should be appended to the existing lookup in Cribl Stream. utwritelookup does not perform any sort of deduplication and just appends the events | - | False |
| create_empty | Whether utwritelookup should create an empty lookup in Cribl Stream if no events were piped into the command | - | False |
| overwrite_if_empty | Whether utwritelookup should overwrite an existing lookup with an empty lookup if no events were piped into the command | - | False |
Examples
Creating a lookup based on search results
To create a lookup containing all hosts sending data to Splunk and the earliest and latest event, run the search as visible below:
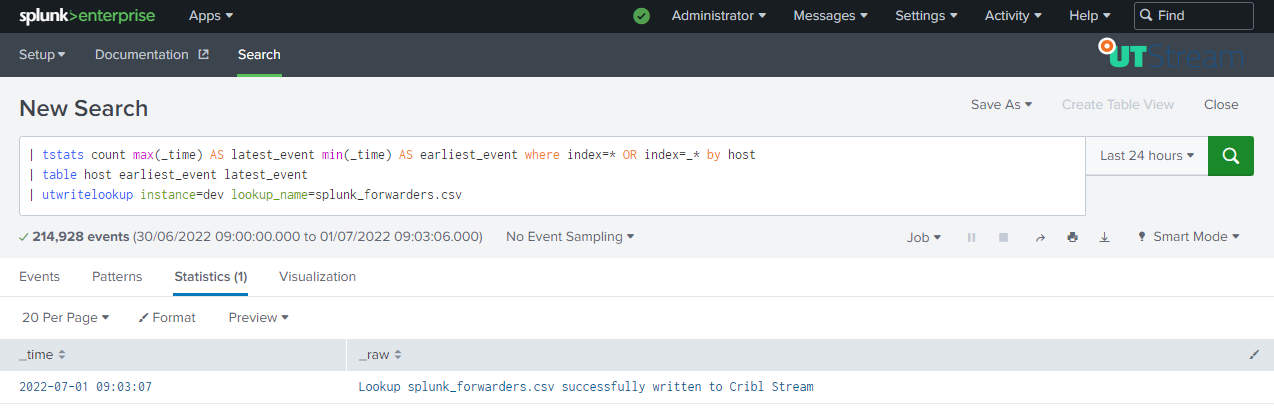
Copying a lookup in Splunk to Cribl Stream
To copy a lookup from Splunk to Cribl Stream run a search similar to the one visible in the screenshot below:
